Análisis sistemático de protocolos de seguridad de datos en el cloud computing: Revisión de la literatura
Contenido principal del artículo
Resumen
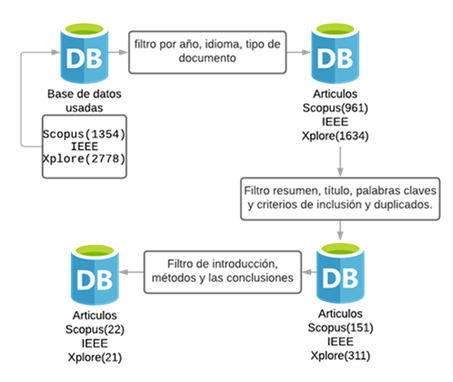
Este trabajo presenta una revisión sistemática de estudios relevantes publicados entre los años 2019 y 2024, centrados en los protocolos de seguridad de datos en entornos de computación en la nube. La selección de artículos se realizó mediante criterios rigurosos, con el objetivo de identificar las características más destacadas de estos protocolos y sus aplicaciones actuales. Se analizan tanto sus ventajas como los mecanismos criptográficos utilizados para proteger la información sensible, entre los que se encuentran AES, RSA y ECC. Adicionalmente, se considera el creciente uso de Kubernetes como herramienta de orquestación de contenedores, reconociendo su importancia dentro de las infraestructuras modernas en la nube. En este contexto, se examinan diversas publicaciones que evidencian limitaciones en su implementación, tales como la gestión inadecuada de privilegios y la dependencia de soluciones de terceros. El estudio ofrece una visión integral que facilite la comprensión de los desafíos actuales y oriente la búsqueda de soluciones que fortalezcan la seguridad en entornos cloud.
##plugins.themes.bootstrap3.displayStats.downloads##
Detalles del artículo
Sección

Esta obra está bajo una licencia internacional Creative Commons Atribución 4.0.
Los autores que publican en esta revista están de acuerdo con los siguientes términos: Los autores conservan los derechos de autor y garantizan a la revista el derecho de ser la primera publicación del trabajo al igual que licenciado bajo una Creative Commons Attribution License que permite a otros compartir el trabajo con un reconocimiento de la autoría del trabajo y la publicación inicial en esta revista. Los autores pueden establecer por separado acuerdos adicionales para la distribución no exclusiva de la versión de la obra publicada en la revista (por ejemplo, situarlo en un repositorio institucional o publicarlo en un libro), con un reconocimiento de su publicación inicial en esta revista. Se permite y se anima a los autores a difundir sus trabajos electrónicamente (por ejemplo, en repositorios institucionales o en su propio sitio web) antes y durante el proceso de envío, ya que puede dar lugar a intercambios productivos, así como a una citación más temprana y mayor de los trabajos publicados.Cómo citar
Referencias
[1] A. Patel, N. Shah, D. Ramoliya and A. Nayak, "A detailed review of Cloud Security: Issues, Threats & Attacks," 2020 4th International Conference on Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, pp. 758-764, 2020, doi: 10.1109/ICECA49313.2020.9297572.
[2] Sinchana, M.K., Savithramma, R.M, “ Survey on Cloud Computing Security” Innovations in Computer Science and Engineering. Lecture Notes in Networks and Systems, Springer, Singapore, vol 103, pp 1-6, https://doi.org/10.1007/978-981-15-2043-3_1
[3] R. Kumar and M. P. S. Bhatia, "A Systematic Review of the Security in Cloud Computing: Data Integrity, Confidentiality and Availability," 2020 IEEE International Conference on Computing, Power and Communication Technologies (GUCON), Greater Noida, India, pp. 334-337, 2020, doi: 10.1109/GUCON48875.2020.9231255.
[4] P. R. Tomás Gabriel, “Seguridad Informática en la Adopción de Cloud Computing en la Industria Alimentaria”, Rev. Boaciencia. Negocios Tecnol., vol. 1, n.º 2, p. 93, 2021.
[5] A. M. Torres González, “Análisis de los componentes de seguridad informática en la implementación de cloud computing en pequeñas y medianas empresas colombianas”, Monografía, UNIVIERSIDAD. NACIONAL ABIERTA Y A DISTANCIA - UNAD ESCUELA DE CIENCIAS BÁSICAS, TECNOLGÍA E INGENIERÍA., Bogotá, 2020.
[6] J. Liu, Q. Zhong, R. Sun, X. Du and M. Guizani, "A Secure and Efficient Medical Data Sharing Protocol for Cloud-Assisted WBAN" in 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 2019, pp. 1-6, doi: 10.1109/GLOBECOM38437.2019.9014307.
[7] P. Zhang, H. Chi, J. Wang, and Y. Shang, "Data security protocol with blind factor in cloud environment" in Information, vol. 12, no. 9, art. no. 340, 2021, doi: 10.3390/info12090340.
[8] V. Kumar, M. S. Mahmoud, A. Alkhayyat, J. Srinivas, M. Ahmad, and A. Kumari, "RAPCHI: Robust authentication protocol for IoMT-based cloud-healthcare infrastructure" in The Journal of Supercomputing, vol. 78, no. 14, pp. 16167–16196, 2022, doi: 10.1007/s11227-022-04513-4.
[9] S. N. Prasad and C. Rekha, "Blockchain-based IAS protocol to enhance security and privacy in cloud computing," in Measurement: Sensors, vol. 28, art. no. 100813, 2023, doi: 10.1016/j.measen.2023.100813.
[10] B. D. Deebak and F. Al-Turjman, "Smart mutual authentication protocol for cloud-based medical healthcare systems using internet of medical things," in IEEE Journal on Selected Areas in Communications, vol. 39, no. 2, pp. 346–360, 2021, doi: 10.1109/jsac.2020.3020599.
[11] O. Ruan, X. Huang and H. Mao, "An efficient private set intersection protocol for the cloud computing environments," in 2020 IEEE 6th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing (HPSC), and IEEE International Conference on Intelligent Data and Security (IDS), 2020, doi: 10.1109/BigDataSecurity-HPSC-IDS49724.2020.00053.
[12] S. Farahmandian and D. B. Hoang, "A policy-based interaction protocol between software defined security controller and virtual security functions," in 2020 4th Cyber Security in Networking Conference (CSNet), 2020,doi: 10.1109/CSNet50428.2020.9265460.
[13] A. Delham Algarni, F. Algarni, S. Ullah Jan and N. Innab, "LSP–eHS: A lightweight and secure protocol for e-healthcare system," IEEE Access: Practical Innovations, Open Solutions, vol. 12, pp. 156849–156866, 2024, doi: 10.1109/access.2024.3477922.
[14] S. S. Manivannan, P. Shashidhar, C. Vanmathi and P. M. D. R. Vincent, "Multi authority privacy preserving protocol in cloud computing authentication using grouping algorithm and EDAC-MAC" in 2019 2nd International Conference on Intelligent Computing, Instrumentation and Control Technologies (ICICICT), 2019 doi: 10.1109/ICICICT46008.2019.8993380.
[15] S. Itoo, A. A. Khan, V. Kumar, A. Alkhayyat, M. Ahmad and J. Srinivas, "CKMIB: Construction of key agreement protocol for cloud medical infrastructure using blockchain" IEEE Access: Practical Innovations, Open Solutions, vol. 10, pp. 67787–67801, 2022, doi: 10.1109/access.2022.3185016.
[16] S. Han, K. Han and S. Zhang, "A data sharing protocol to minimize security and privacy risks of cloud storage in big data era" in IEEE Access: Practical Innovations, Open Solutions, vol. 7, pp. 60290–60298, 2019, doi: 10.1109/access.2019.2914862.
[17] J. Liang, Z. Qin, J. Ni, X. Lin and X. Shen, "Efficient and Privacy-Preserving Outsourced SVM Classification in Public Cloud," ICC 2019 - 2019 IEEE International Conference on Communications (ICC), Shanghai, China, 2019, pp. 1-6, doi: 10.1109/ICC.2019.8761610.
[18] H. Wang, D. He and J. Han, "VOD-ADAC: Anonymous distributed fine-grained access control protocol with verifiable outsourced decryption in public cloud" in IEEE Transactions on Services Computing, vol. 13, no. 3, pp. 572–583, 2020, doi: 10.1109/tsc.2017.2687459.
[19] R. Stoyanov, A. Reber, D. Ueno, M. Clapiński, A. Vagin and R. Bruno, "Towards efficient end-to-end encryption for container checkpointing systems." in Proceedings of the 15th ACM SIGOPS Asia-Pacific Workshop on Systems, pp. 60–66. 2024. DOI: 10.1145/3678015.3680477.
[20] M. Femminella, M. Palmucci, G. Reali, and M. Rengo, "Attribute-based management of secure Kubernetes cloud bursting." un IEEE Open Journal of the Communications Society, vol. 5, pp. 1276–1298, 2024, doi: 10.1109/ojcoms.2024.3367461.
[21] M. V. Le, S. Ahmed, D, Williams and H. Jamjoom, "Securing container-based clouds with syscall-aware scheduling." in Proceedings of the ACM Asia Conference on Computer and Communications Security, pp. 812–826. 2023 . DOI: 10.1145/3579856.3582835.
[22] A. Sadiq, H. J. Syed, A. A. Ansari, A. O. Ibrahim, M. Alohaly and M. Elsadig, "Detection of Denial of service attack in cloud based Kubernetes using eBPF." in Applied Sciences (Basel, Switzerland), 13(8), p 4700. 2023. DOI: 10.3390/app13084700.
[23] N. Pecka, L. Ben Othmane and A. Valani, "Privilege escalation attack scenarios on the DevOps pipeline within a Kubernetes environment." in Proceedings of the International Conference on Software and System Processes and International Conference on Global Software Engineering, pp 45–49.2022 .DOI: 10.1145/3529320.3529325.
[24] J. Mahboob, and J. Coffman, "A Kubernetes CI/CD pipeline with asylo as a trusted execution environment abstraction framework." in 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC). 2021. DOI: 10.1109/CCWC51732.2021.9376148.
[25] H. Lim, Y. Kim and K. Sun, "Service management in virtual machine and container mixed environment using service mesh." in 2021 International Conference on Information Networking (ICOIN). 2021. DOI: 10.1109/ICOIN50884.2021.9333888.
[26] S. Shringarputale, P. McDaniel, K. Butler and T. La Porta, "Co-residency Attacks on Containers are Real." in Proceedings of the 2020 ACM SIGSAC Conference on Cloud Computing Security Workshop. 2020. DOI: 10.1145/3411495.3421357.
[27] D. Bringhenti, G, Marchetto, R. Sisto, F. Valenza and J. Yusupov, "Introducing programmability and automation in the synthesis of virtual firewall rules." in 2020 6th IEEE Conference on Network Softwarization (NetSoft), 2020, DOI: 10.1109/NetSoft48620.2020.9165434.
[28] A. F. Baarzi, G. Kesidis, D. Fleck and A. Stavrou, "Microservices made attack-resilient using unsupervised service fissioning." Proceedings of the 13th European Workshop on Systems Security, 2020, DOI: 10.1145/3380786.3391395.
[29] A. Borisova, V. Shvetcova, and O. Borisenko, "Adaptation of the TOSCA standard model for the Kubernetes container environment," in 2020 Ivannikov Memorial Workshop (IVMEM), 2020. DOI: 10.1109/IVMEM51402.2020.00008.
[30] T. Heo, J. H. An, and Y. Kim, "Design and implementation of migration manager between cloud edge platforms," in Proceedings of the International Conference on Research in Adaptive and Convergent Systems, 2020. DOI: 10.1145/3400286.3418279.
[31] D. Y. Yuan, and T. Wildish, "Bioinformatics application with Kubeflow for batch processing in clouds," in Lecture Notes in Computer Science, Springer International Publishing, 2020, pp. 355–367. DOI: 10.1007/978-3-030-59851-8_24.
[32] A. Brito, C. Fetzer, S. Köpsell, P. Pietzuch, M. Pasin, P. Felber, K. Fonseca, M. Rosa, L. Gomes Jr, R. Riella, C. Prado, L. F. Rust, D. E. Lucani, M. Sipos, L. Nagy and M. Fehér, "Secure end-to-end processing of smart metering data," in Journal of Cloud Computing: Advances, Systems and Applications, vol. 8, no. 1, 2019. DOI: 10.1186/s13677-019-0141-z.
[33] N. Surantha and F. Ivan, "Secure Kubernetes networking design based on zero trust model: A case study of financial service enterprise in Indonesia," in Innovative Mobile and Internet Services in Ubiquitous Computing, Springer International Publishing, pp. 348–361. 2020. DOI: 10.1007/978-3-030-22263-5_34.
[34] G. P. Fernandez and A. Brito, "Secure container orchestration in the cloud: Policies and implementation," in Proceedings of the 34th ACM/SIGAPP Symposium on Applied Computing, pp. 1635–1642. 2019. DOI: 10.1145/3297280.3297296.
[35] B. Thurgood and R. G. Lennon, "Cloud computing with Kubernetes cluster elastic scaling," in Proceedings of the 3rd International Conference on Future Networks and Distributed Systems, pp. 1–6. 2019. DOI: 10.1145/3341325.3341995.
[36] C. W. Tien, T. Y. Huang, C. W. Tien, T. C. Huang and S. Y. Kuo, "KubAnomaly: Anomaly detection for the Docker orchestration platform with neural network approaches," in Engineering Reports: Open Access, vol. 1, no. 5, 2019. DOI: 10.1002/eng2.12080.
[37] H. Hamzeh, S. Meacham and K. Khan, "A new approach to calculate resource limits with fairness in Kubernetes," in 2019 First International Conference on Digital Data Processing (DDP), 2019. Doi: 10.1145/3366615.3368356
[38] S. Suneja, A. Kanso and C. Isci, "Can container fusion be securely achieved?" in Proceedings of the 5th International Workshop on Container Technologies and Container Clouds, 2019, doi: 10.1145/3366615.3368356.
[39] B. Chun, J. Ha, S. Oh, H. Cho and M. Jeong, "Kubernetes Enhancement for 5G NFV Infrastructure" in 2019 International Conference on Information and Communication Technology Convergence (ICTC), 2019, doi: 10.1109/ICTC46691.2019.8939817.
[40] A. Yeboah-Ofori, A. Jafar, T. Abisogun, I. Hilton, W. Oseni and A. Musa, "Data security and governance in multi-cloud computing environment" in 2024 11th International Conference on Future Internet of Things and Cloud (FiCloud),pp. 215–222, 2024. doi: 10.1109/FiCloud62933.2024.00040.
[41] D. Soldani, P. Nahi, H. Bour, S. Jafarizadeh, M. F. Soliman, L. Di Giovanna, F. Monaco, G. Ognibene and F. Risso, "EBPF: A new approach to cloud-native observability, networking and security for current (5G) and future mobile networks (6G and beyond) " in IEEE Access: Practical Innovations, Open Solutions, vol. 11, pp. 57174–57202, 2023, doi: 10.1109/access.2023.3281480.
[42] A. Blaise and F. Rebecchi, "Stay at the Helm: secure Kubernetes deployments via graph generation and attack reconstruction," un 2022 IEEE 15th International Conference on Cloud Computing (CLOUD), 2022, doi: 10.1109/CLOUD55607.2022.00022.
[43] G. Budigiri, C. Baumann, J. T. Muhlberg, E. Truyen and W. Joosen, "Network policies in Kubernetes: Performance evaluation and security analysis," un 2021 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), 2021, doi: 10.1109/EuCNC/6GSummit51104.2021.9482526.
[44] M. Ul Haque, M. M. Kholoosi and M. A. Babar, "KGSecConfig: A knowledge graph based approach for secured container orchestrator configuration," in 2022 IEEE International Conference on Software Analysis, Evolution and Reengineering (SANER), 2022, doi: 10.1109/SANER53432.2022.00057.
[45] S. Lee and J. Nam, "Kunerva: Automated network policy discovery framework for containers" in IEEE Access: Practical Innovations, Open Solutions, vol. 11, pp. 95616–95631, 2023, doi: 10.1109/ACCESS.2023.3310281..
[46] J. M. Parra-Ullauri, L. F. Gonzalez, A. Bravalheri, R. Hussain, X. Vasilakos, I. Vidal, F. Valera, R. Nejabati, and D. Simeonidou, "Privacy preservation in Kubernetes-based federated learning: A networking approach," in IEEE INFOCOM 2023 - IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), pp. 1–7, 2023, doi: 10.1109/INFOCOMWKSHPS57453.2023.10225925.
[47] F. Hussain, W. Li, B. Noye, S. Sharieh and A. Ferworn, "Intelligent Service Mesh Framework for API Security and Management," in 2019 IEEE 10th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), 2019, doi: 10.1109/IEMCON.2019.8936216.
[48] J. Santos, E. Truyen, C. Baumann, F. De Turck, G. Budigiri and W. Joosen, "Towards intent-based scheduling for performance and security in edge-to-cloud networks," in 2024 27th Conference on Innovation in Clouds, Internet and Networks (ICIN), pp. 222–227, 2024, doi: 10.1109/ICIN60470.2024.10494432.
[49] R. R. Karn, P. Kudva, H. Huang, S. Suneja and I. M. Elfadel, "Cryptomining detection in container clouds using system calls and explainable machine learning," in IEEE Transactions on Parallel and Distributed Systems: A Publication of the IEEE Computer Society, vol. 32, no. 3, pp. 674–691, 2021, doi: 10.1109/tpds.2020.3029088.