Application of artificial intelligence in the Internet of Things: a documentary study
Main Article Content
Abstract
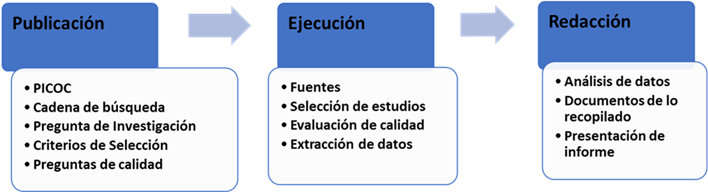
The convergence of the Internet of Things (IoT) and Artificial Intelligence (AI) has catalyzed substantial advancements across multiple sectors, including agriculture, security, healthcare, home automation, and resource management. This paper presents a systematic literature review aimed at identifying key applications, AI techniques, and benefits resulting from the integration of these technologies. The review process was conducted in accordance with the PRISMA methodology, encompassing publication selection, data extraction, and analysis. Out of 725 initially retrieved records, 53 studies were selected for detailed examination. The results indicate that multisensor systems represent 28.85% of the reported applications, followed by IoT security (21.15%) and smart cities (15.38%). In terms of AI techniques, multisensor data fusion was the most frequently employed (40.38%), followed by deep neural networks (19.23%) and support vector machines (15.38%). Most of the reviewed studies report accuracy levels of 90% or higher. These findings highlight the critical role of AI in enhancing IoT systems and identify the domains with the highest potential for future development.
Downloads
Article Details

This work is licensed under a Creative Commons Attribution 4.0 International License.
Authors who publish in this journal agree to the following terms: Authors retain the copyright and guarantee the journal the right to be the first publication of the work, as well as, licensed under a Creative Commons Attribution License that allows others share the work with an acknowledgment of the authorship of the work and the initial publication in this journal. Authors may separately establish additional agreements for the non-exclusive distribution of the version of the work published in the journal (for example, placing it in an institutional repository or publishing it in a book), with acknowledgment of its initial publication in this journal. Authors are allowed and encouraged to disseminate their work electronically (for example, in institutional repositories or on their own website) before and during the submission process, as it may lead to productive exchanges as well as further citation earliest and oldest of published works.
How to Cite
References
[1] C. Kim and J. Lee, “Discovering patterns and trends in customer service technologies patents using large language model,” Heliyon, vol. 10, no. 14, Jul. 2024, doi: 10.1016/j.heliyon.2024.e34701.
[2] C. Li, S. He, Y. Tian, S. Sun, and L. Ning, “Does the bank’s FinTech innovation reduce its risk-taking? Evidence from China’s banking industry,” Journal of Innovation and Knowledge, vol. 7, no. 3, Jul. 2022, doi: 10.1016/j.jik.2022.100219.
[3] M. García Munguía, H. D. Molina Ruíz, M. Cornejo Velázquez, S. S. Moreno Gutiérrez, and J. L. Alvarado Reséndiz, “Internet de las cosas,” TEPEXI Boletín Científico de la Escuela Superior Tepeji del Río, vol. 7, no. 14, 2020, doi: 10.29057/estr.v7i14.5698.
[4] J. M. Ibrahim, A. Karami, and F. Jafari, “A secure smart home using Internet-of-Things,” in ACM International Conference Proceeding Series, Association for Computing Machinery, Oct. 2017, pp. 69–74. doi: 10.1145/3149572.3149577.
[5] V. D. Ganda, R. Ritika, P. S. Mehra, and D. Chawla, “A Systematic Review on Internet of Things (IoT) Security: Applications, Architecture, Challenges and Solutions,” in 2024 1st International Conference on Advanced Computing and Emerging Technologies, ACET 2024, Institute of Electrical and Electronics Engineers Inc., 2024. doi: 10.1109/ACET61898.2024.10729954.
[6] N. Hasteer, R. Sindhwani, R. Sharma, and P. L. Singh, “A fuzzy Interpretive Structural Modeling approach for implementing IoT and achieving the United Nations Sustainable Development Goals,” Decision Analytics Journal, vol. 8, Sep. 2023, doi: 10.1016/j.dajour.2023.100313.
[7] I. Francisco Javier Flores Zermeño, E. Gonzalo Cossio Franco, and F. Javier Flores, “Aplicaciones, Enfoques y Tendencias del Internet de las Cosas (IoT): Revisión Sistemática de la Literatura,” Congreso Internacional de Investigación Academia Journals Hidalgo, vol. 13, no. 9, p. 568, 2021.
[8] S. P. H. Boroujeni et al., “A comprehensive survey of research towards AI-enabled unmanned aerial systems in pre-, active-, and post-wildfire management,” Information Fusion, vol. 108, Aug. 2024, doi: 10.1016/j.inffus.2024.102369.
[9] M. Simon, D. L. Iveta, L. Huraj, and J. Pospichal, “Multi-Hub Location Heuristic for Alert Routing,” IEEE Access, vol. 7, pp. 40369–40379, 2019, doi: 10.1109/ACCESS.2019.2907161.
[10] H. H. Xiao, W. K. Yang, J. Hu, Y. P. Zhang, L. J. Jing, and Z. Y. Chen, “Significance and methodology: Preprocessing the big data for machine learning on TBM performance,” Underground Space (China), vol. 7, no. 4, pp. 680–701, Aug. 2022, doi: 10.1016/j.undsp.2021.12.003.
[11] A. Telukdarie, M. Munsamy, T. Katsumbe, and X. Maphisa, “Smart value chain tool advancing sustainability in the FoodBev manufacturing industry,” J Clean Prod, vol. 441, Feb. 2024, doi: 10.1016/j.jclepro.2024.140871.
[12] B. G. Martini et al., “A computational model for ubiquitous intelligent services in indoor agriculture,” in Proceedings of the 25th Brazillian Symposium on Multimedia and the Web, WebMedia 2019, Association for Computing Machinery, Inc, Oct. 2019, pp. 497–500. doi: 10.1145/3323503.3360641.
[13] Y. R. Julio et al., “Cloud Framework for Precision Agriculture: Applying ‘Kernel Trick’ Techniques in Support Vector Machines via MQTT and IoT,” in 2024 IEEE Colombian Conference on Communications and Computing, COLCOM 2024 - Proceedings, Institute of Electrical and Electronics Engineers Inc., 2024. doi: 10.1109/COLCOM62950.2024.10720254.
[14] M. AL-Hawawreh, E. Sitnikova, and F. Den Hartog, “An efficient intrusion detection model for edge system in brownfield industrial internet of things,” in ACM International Conference Proceeding Series, Association for Computing Machinery, Aug. 2019, pp. 83–87. doi: 10.1145/3361758.3361762.
[15] H. Xiong et al., “Efficient and Privacy-Enhanced Asynchronous Federated Learning for Multimedia Data in Edge-based IoT,” ACM Transactions on Multimedia Computing, Communications, and Applications, Aug. 2024, doi: 10.1145/3688002.
[16] A. Bhavani and V. Nithya, “Cryptographic Algorithm for Enhancing Data Security in Wireless IoT Sensor Networks,” Intelligent Automation and Soft Computing, vol. 36, no. 2, pp. 1381–1393, 2023, doi: 10.32604/iasc.2023.029397.
[17] A. Saeed, A. Ahmadinia, A. Javed, and H. Larijani, “Intelligent intrusion detection in low-power IoTs,” ACM Trans Internet Technol, vol. 16, no. 4, Dec. 2016, doi: 10.1145/2990499.
[18] L. Stuermer and R. Martin, “Characterization of technologies in digital health applied in vision care,” J Optom, vol. 15, pp. S70–S81, Jan. 2022, doi: 10.1016/j.optom.2022.09.005.
[19] A. M. Shamsan Saleh, “Blockchain for secure and decentralized artificial intelligence in cybersecurity: A comprehensive review,” Sep. 01, 2024, Zhejiang University. doi: 10.1016/j.bcra.2024.100193.
[20] L. Nie et al., “Intrusion Detection for Secure Social Internet of Things Based on Collaborative Edge Computing: A Generative Adversarial Network-Based Approach,” IEEE Trans Comput Soc Syst, vol. 9, no. 1, pp. 134–145, Feb. 2022, doi: 10.1109/TCSS.2021.3063538.
[21] C. Yang, X. Wang, and S. Mao, “Unsupervised Detection of Apnea Using Commodity RFID Tags with a Recurrent Variational Autoencoder,” IEEE Access, vol. 7, pp. 67526–67538, 2019, doi: 10.1109/ACCESS.2019.2918292.
[22] R. Tsopra et al., “Putting undergraduate medical students in AI-CDSS designers’ shoes: An innovative teaching method to develop digital health critical thinking,” Int J Med Inform, vol. 171, Mar. 2023, doi: 10.1016/j.ijmedinf.2022.104980.
[23] A. Kumar et al., “Digging DEEP: Futuristic building blocks of omni-channel healthcare supply chains resiliency using machine learning approach,” J Bus Res, vol. 162, Jul. 2023, doi: 10.1016/j.jbusres.2023.113903.
[24] M. Blaivas, “Artificial Intelligence and Ultrasonography,” Medicina digital, no. Vol. 31 No. 1, May 2024, doi: 10.24950/rspmi.2585.
[25] D. Kim, S. Cho, L. Tamil, D. J. Song, and S. Seo, “Predicting asthma attacks: Effects of indoor PM concentrations on peak expiratory flow rates of asthmatic children,” IEEE Access, vol. 8, pp. 8791–8797, 2020, doi: 10.1109/ACCESS.2019.2960551.
[26] D. Meana-Llorian, C. G. Garcia, B. C. P. G-Bustelo, J. M. C. Lovelle, and V. H. M. Garcia, “IntelliSenses: Sintiendo Internet de las Cosas,” in Iberian Conference on Information Systems and Technologies, CISTI, IEEE Computer Society, Jul. 2016. doi: 10.1109/CISTI.2016.7521551.
[27] A. Karapetyan, S. Chi-Kin Chau, K. Elbassioni, S. K. Azman, and M. Khonji, “Multisensor adaptive control system for IoT-empowered smart lighting with oblivious mobile sensors,” ACM Trans Sens Netw, vol. 16, no. 1, Dec. 2019, doi: 10.1145/3369392.
[28] S. Akter, Y. K. Dwivedi, S. Sajib, K. Biswas, R. J. Bandara, and K. Michael, “Algorithmic bias in machine learning-based marketing models,” J Bus Res, vol. 144, pp. 201–216, May 2022, doi: 10.1016/j.jbusres.2022.01.083.
[29] Y. C. Huang, Y. T. Cheng, R. H. Liang, J. Y. J. Hsu, and L. L. Chen, “Thing Constellation Visualizer: Exploring Emergent Relationships of Everyday Objects,” Proc ACM Hum Comput Interact, vol. 5, no. CSCW2, Oct. 2021, doi: 10.1145/3479866.
[30] A. G. Qoutb and E. G. Friedman, “MTJ magnetization switching mechanisms for IoT applications,” in Proceedings of the ACM Great Lakes Symposium on VLSI, GLSVLSI, Association for Computing Machinery, May 2018, pp. 347–352. doi: 10.1145/3194554.3194624.
[31] X. Zuo, X. Yang, Z. Dou, and J. R. Wen, “RUCIR at TREC 2019: Conversational Assistance Track,” in 28th Text REtrieval Conference, TREC 2019 - Proceedings, National Institute of Standards and Technology (NIST), 2019. doi: 10.1145/1122445.1122456.
[32] F. Ferreira, V. Amaral, and F. Brito e Abreu, “Digital twinning for smart restoration of classic cars,” in Procedia Computer Science, Elsevier B.V., 2024, pp. 2521–2530. doi: 10.1016/j.procs.2024.02.070.
[33] M. Q. Huang, J. Ninić, and Q. B. Zhang, “BIM, machine learning and computer vision techniques in underground construction: current status and future perspectives.” doi: 10.1016/j.tust.2020.103677.
[34] M. Perno, L. Hvam, and A. Haug, “A machine learning digital twin approach for critical process parameter prediction in a catalyst manufacturing line,” Comput Ind, vol. 151, Oct. 2023, doi: 10.1016/j.compind.2023.103987.
[35] B. M. Sri Madhu, K. Kanagotagi, and Devansh, “IoT based Automatic Attendance Management System,” in International Conference on Current Trends in Computer, Electrical, Electronics and Communication, CTCEEC 2017, Institute of Electrical and Electronics Engineers Inc., Sep. 2018, pp. 83–86. doi: 10.1109/CTCEEC.2017.8455099.
[36] G. De Haan, “Educating Creative Technology for the Internet of Things-Research and Practice-oriented Approaches Compared,” in MIDI 15: Actas del Congreso Multimedia, Interacción, Diseño e Innovación, pp. 1–7. doi: 10.1145/2814464.2814469.
[37] N. R. Beckham, L. J. Akeh, G. N. P. Mitaart, and J. V. Moniaga, “Determining factors that affect student performance using various machine learning methods,” in Procedia Computer Science, Elsevier B.V., 2022, pp. 597–603. doi: 10.1016/j.procs.2022.12.174.
[38] E. Anastasiou et al., “Precision farming technologies for crop protection: A meta-analysis,” Smart Agricultural Technology, vol. 5, Oct. 2023, doi: 10.1016/j.atech.2023.100323.
[39] R. Jolak et al., “CONSERVE: A framework for the selection of techniques for monitoring containers security,” Journal of Systems and Software, vol. 186, Apr. 2022, doi: 10.1016/j.jss.2021.111158.
[40] I. Latin and A. Transactions, “IoT Best Practices and their Components: A Systematic Literature Review,” IEEE Latin America Transactions, vol. 20, no. 10, pp. 2217–2228, 2022, doi: 10.1109/TLA.2022.9885169.
[41] S. Akkermans, B. Crispo, W. Joosen, and D. Hughes, “Polyglot cerberOS: Resource security, interoperability and multi-tenancy for IoT services on a multilingual platform,” in ACM International Conference Proceeding Series, Association for Computing Machinery, Nov. 2018, pp. 59–68. doi: 10.1145/3286978.3286997.
[42] A. Kumar, “A novel framework for waste management in smart city transformation with industry 4.0 technologies,” Research in Globalization, vol. 9, Dec. 2024, doi: 10.1016/j.resglo.2024.100234.
[43] P. Arcaini et al., “Smart home platform supporting decentralized adaptive automation control,” in Proceedings of the ACM Symposium on Applied Computing, Association for Computing Machinery, Mar. 2020, pp. 1893–1900. doi: 10.1145/3341105.3373925.
[44] A. Bhardwaj, K. Kaushik, M. Alshehri, A. A.-B. Mohamed, and I. Keshta, “ISF: Security Analysis and Assessment of Smart Home IoT-based Firmware,” ACM Trans Sens Netw, Jan. 2023, doi: 10.1145/3578363.
[45] F. Li, H. Yang, X. Gao, and H. Han, “Towards IoT-based sustainable digital communities,” Intelligent and Converged Networks, vol. 3, no. 2, pp. 190–203, Jun. 2022, doi: 10.23919/ICN.2022.0015.
[46] Y. Wang et al., “IoT-based green-smart photovoltaic system under extreme climatic conditions for sustainable energy development,” Global Energy Interconnection, vol. 7, pp. 836–856, 2024, doi: 10.1016/j.gloei.2024.1.
[47] M. Woschank, D. Steinwiedder, A. Kaiblinger, P. Miklautsch, C. Pacher, and H. Zsifkovits, “The Integration of Smart Systems in the Context of Industrial Logistics in Manufacturing Enterprises,” in Procedia Computer Science, Elsevier B.V., 2022, pp. 727–737. doi: 10.1016/j.procs.2022.01.271.
[48] S. Subramaniam, L. J. Chew, S. C. Haw, and M. T. Bin Ziauddin, “WQMS: A Water Quality Monitoring System using IoT,” in ACM International Conference Proceeding Series, Association for Computing Machinery, Nov. 2019, pp. 177–182. doi: 10.1145/3372422.3372429.
[49] S. Cairone et al., “Integrating artificial intelligence modeling and membrane technologies for advanced wastewater treatment: Research progress and future perspectives,” Science of the Total Environment, vol. 944, Sep. 2024, doi: 10.1016/j.scitotenv.2024.173999.
[50] R. Mahmud, F. L. Koch, and R. Buyya, “Cloud-fog interoperability in IoT-enabled healthcare solutions,” in ACM International Conference Proceeding Series, Association for Computing Machinery, Jan. 2018. doi: 10.1145/3154273.3154347.
[51] J. Enes, R. R. Expósito, J. Fuentes, J. L. Cacheiro, and J. Touriño, “A pipeline architecture for feature-based unsupervised clustering using multivariate time series from HPC jobs,” Information Fusion, vol. 93, pp. 1–20, May 2023, doi: 10.1016/j.inffus.2022.12.017.
[52] K. Zia, S. Al Maskari, D. K. Saini, A. Muhammad, and U. Farooq, “A simulation model demonstrating the impact of social aspects on social internet of things,” in ACM International Conference Proceeding Series, Association for Computing Machinery, Dec. 2019. doi: 10.1145/3366030.3366076.
[53] E. Badakhshan, N. Mustafee, and R. Bahadori, “Application of simulation and machine learning in supply chain management: A synthesis of the literature using the Sim-ML literature classification framework,” Comput Ind Eng, vol. 198, Dec. 2024, doi: 10.1016/j.cie.2024.110649.
[54] E. Pournaras, P. Pilgerstorfer, and T. Asikis, “Decentralized collective learning for self-managed sharing economies,” ACM Transactions on Autonomous and Adaptive Systems, vol. 13, no. 2, Nov. 2018, doi: 10.1145/3277668.
[55] M. Caporuscio, F. Flammini, N. Khakpour, P. Singh, and J. Thornadtsson, “Smart-troubleshooting connected devices: Concept, challenges and opportunities,” Future Generation Computer Systems, vol. 111, pp. 681–697, Oct. 2020, doi: 10.1016/j.future.2019.09.004.
[56] Y. Bandung, M. A. Wicaksono, S. Pribadi, A. Z. R. Langi, and D. Tanjung, “IoT Video Delivery Optimization Through Machine Learning-Based Frame Resolution Adjustment,” ACM Transactions on Multimedia Computing, Communications, and Applications, Sep. 2024, doi: 10.1145/3665929.